Top Web Scraping Software in 2025
Discover top web scraping tools for 2025, comparing features, proxy integration, and scalability to optimize your data extraction efforts.
Post Time:2025-04-25
Step-by-step guide to install and configure NGINX, Apache, or Caddy as a reverse proxy for home servers, complete with SSL, security, and troubleshooting tips.
A reverse proxy sits between the internet and your home-hosted services—websites, media servers, IoT dashboards—and routes incoming requests to the correct internal server based on domain or URL path. It provides a single public endpoint, handles SSL/TLS, adds security controls, and can cache or load-balance traffic. This guide walks through three popular options—NGINX, Apache, and Caddy—with crystal-clear steps so even total beginners can set it up.
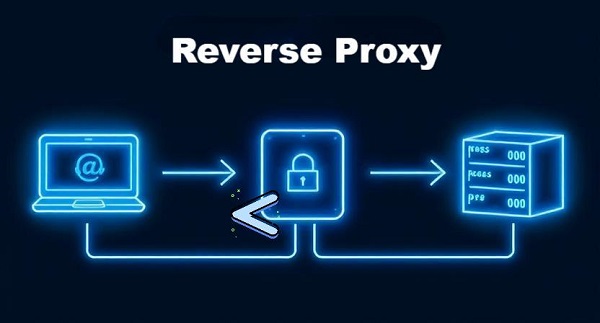
A reverse proxy is a gateway server that:
Unlike a forward proxy (which hides client identities), a reverse proxy hides your internal network structure and consolidates access.
1. Single Access Point
Consolidate multiple services under one domain (e.g., home.example.com/media → Plex, /iot → Home Assistant).
2. Centralized SSL Management
Terminate HTTPS once at the proxy using Let’s Encrypt, rather than on each service.
3. Enhanced Security
Shield backend servers behind firewall rules, enforce authentication, and filter traffic.
4. Load-Balancing & Caching
Distribute requests across multiple instances or cache static content to save bandwidth.
5. Dynamic DNS & NAT Traversal
Works seamlessly with dynamic IP services—no manual reconfiguration if your ISP IP changes.
Remote access to Plex, Nextcloud, Home Assistant
HTTPS termination via Let’s Encrypt
Single entry-point for multiple apps (subdomains or subpaths)
NGINX: High performance, extensive community support
Apache: Familiar for those with LAMP stacks, rich module ecosystem
Caddy: Automatic HTTPS, minimal config
A home server or Raspberry Pi with a static LAN IP (e.g., 192.168.1.10)
Router port-forwarding set for TCP 80 and 443 → that IP
Up-to-date Ubuntu/Debian or similar OSbash
bash
sudo apt update && sudo apt upgrade -y

bash
sudo apt install nginx -y
Edit /etc/nginx/sites-available/reverse.conf:
nginx
server {
listen 80;
server_name plex.example.com;
location / {
proxy_pass http://192.168.1.20:32400; # Plex on LAN
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
}
}
Enable the site and reload:
bash
sudo ln -s /etc/nginx/sites-available/reverse.conf /etc/nginx/sites-enabled/
sudo nginx -t && sudo systemctl reload nginx
bash
sudo apt install certbot python3-certbot-nginx -y
sudo certbot --nginx -d plex.example.com
Follow prompts; Certbot will edit your NGINX config, handle renewals.
bash
sudo apt install apache2 -y
sudo a2enmod proxy proxy_http proxy_balancer lbmethod_byrequests ssl
Edit /etc/apache2/sites-available/reverse.conf:
apache
<VirtualHost *:80>
ServerName nextcloud.example.com
ProxyPreserveHost On
ProxyPass / http://192.168.1.30:8080/
ProxyPassReverse / http://192.168.1.30:8080/
</VirtualHost>
Enable and reload:
bash
sudo a2ensite reverse.conf
sudo systemctl reload apache2
bash
sudo apt install certbot python3-certbot-apache -y
sudo certbot --apache -d nextcloud.example.com
Apache will configure SSL directives automatically.
bash
sudo apt install -y debian-keyring debian-archive-keyring apt-transport-https
curl -1sLf 'https://dl.cloudsmith.io/public/caddy/stable/gpg.key' | sudo apt-key add -
curl -1sLf 'https://dl.cloudsmith.io/public/caddy/stable/debian.deb.txt' | sudo tee /etc/apt/sources.list.d/caddy-stable.list
sudo apt update
sudo apt install caddy -y
Edit /etc/caddy/Caddyfile:
css
plex.example.com {
reverse_proxy 192.168.1.20:32400
}
nextcloud.example.com {
reverse_proxy 192.168.1.30:8080
}
Caddy handles HTTPS automatically.
Reload Caddy:
bash
sudo systemctl reload caddy
Use DNS-based load balancing to route traffic through the fastest edge node before it hits your reverse proxy.
Add HTTP headers in NGINX (add_header X-Frame-Options SAMEORIGIN) or Apache (Header always set Strict-Transport-Security "max-age=31536000;") to reduce attack surface.
Feed NGINX/Apache/Caddy logs into Grafana via a local metrics exporter for real-time dashboards.
Each solution has strengths:
On a home network, Caddy’s simplicity is ideal for novices, while power users may prefer NGINX’s fine-grained tuning. Keep systems updated, secure your TLS keys, and monitor access logs to catch anomalies early.
A forward proxy sits between client and internet, while a reverse proxy sits between internet and your servers.
Enforce HTTPS, add security headers, limit allowed hostnames, and enable rate limiting.
Forward TCP 80 and 443 from WAN to your proxy server’s LAN IP.
Yes—use multiple server_name (NGINX) or VirtualHost (Apache) blocks, or list them in your Caddyfile.
Ensure the backend service is running, correct proxy_pass IP/port, and check firewall rules.
Next >